Surviving Windows 8 annoyances with HiDrop
Post by Jacques Bensimon:
Some Windows 8.x annoyances you may be up against, with solutions.
(1) By default, Windows 8 administrative shares (C$, Admin$, etc.) cannot be accessed from a remote computer, regardless of any firewall considerations.
The solution:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersionPoliciesSystem]
"LocalAccountTokenFilterPolicy"=dword:00000001
Although this looks like a policy, it’s not exposed by any policy template, so the entry has to be made manually.
(2) By default, a process that’s been “Run as administrator” (more about that later) cannot “see” or access drive mappings created by a “non-admin” process such as Explorer or a normal CMD process, even if the mappings are persistent.
The solution:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersionPoliciesSystem]
"EnableLinkedConnections"=dword:00000001
Again, this setting is not available via any policy template and has to be made manually. It also requires a reboot (I forget if (1) does, but you’ll want both anyway). Unlike (1), I’m pretty sure this one and the one that follows apply to Windows Server 2012 as well. They also apply to Windows 7 and 2008 R2 if you don’t configure the lowest UAC level possible.
(3) This one really annoys me and required a new utility to get around: you cannot drag-and-drop a file from an Explorer window to an “Administrator” command prompt, a consequence of the more general principle that a process that’s been “Run as administrator” will not accept drop messages (and most other types of window messages) from normal processes.
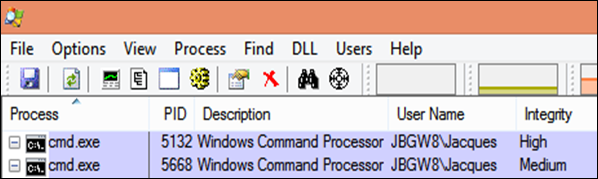
Before I describe the workaround, let me clarify something about the wildly inaccurate misnomer that is the “Run as administrator” launch option: as you can see from the following partial screenshot of “Process Explorer” displaying information about a command window that’s been “Run as administrator” and one launched normally, there is in fact no difference in the user name that owns the process (so there’s no “Run As” going on here involving an actual Administrator account and a secondary logon) – the difference is in that last column (which I encourage you to add to your Process Explorer windows) labeled “Integrity” (for “Integrity Level”, which you can read all about at here) and is part of a process isolation feature that prevents processes from sending messages to or hooking processes running at higher integrity levels than themselves. When UAC is turned all the way down in Windows 7 and Windows 2008 R2, all processes run at the High integrity level, but in Windows 8 and Server 2012, even with UAC turned down to its minimum level, most processes (including the shell itself and therefore all the processes launched normally from the shell) run at the Medium integrity level unless “Run as administrator” is used explicitly (via context menu or shortcut option) or the executable contains a manifest that requests the High integrity level (which you’ll recognize by that little “UAC shield” overlay that Explorer applies to its icon).
The solution:
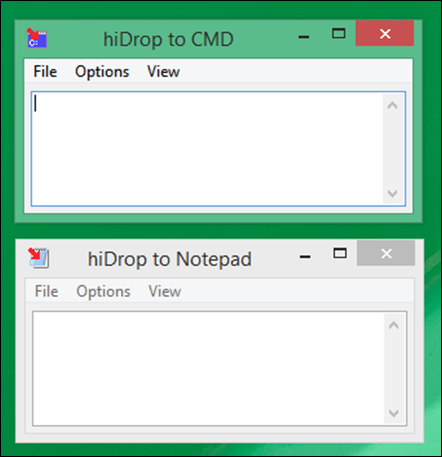
This is where the attached “hiDrop” utility (for “high integrity Drop”) comes in: it runs at the High integrity level but uses the appropriate APIs to allow drop messages from lower integrity processes, in particular from Explorer, and then turns around and drops whatever it receives into the last CMD window to have focus, a sort of “proxy drop”. As long as I was at it, I added the option of dropping instead into the last Notepad window to have focus (useful when you want to drop fully qualified filenames rather than file contents into Notepad). You can run two simultaneous instances of hiDrop with different targets in order to access both capabilities simultaneously (as in the screenshot below). Since hiDrop allows dragging multiple files simultaneously, it also has options for separating multiple filenames with either a space (the default) or a newline (only allowed when Notepad is the target – too dangerous otherwise), as well as options for enclosing file paths in double-quotes always, never or only when there is a space in the path (“smart quoting”). The multiple-file drag-and-drop capability is useful for example when you want to capture the results of an Explorer search window.
If you can think of any other useful features, I’ll be glad to entertain them. (Leave comments below)
One last little tidbit related to process integrity levels: since there are High and Medium integrity levels available, you can guess that Low is another possibility (and if you read the article linked above, you’ll see that there are in fact two others: Untrusted at the low end, and System at the high end). For example, the iexplore.exe processes corresponding to the various tabs of IE windows all run at the Low integrity level, as do some Java-related processes and some Adobe Acrobat, Flash and Shockwave processes). Well, if you’ve ever wondered what the %USERPROFILE%\AppData\LocalLow folder and the HKCUSoftwareAppDataLow Registry key are all about, they’re pretty much the only places to which processes running at the Low integrity level are (by default) allowed to write. So, if not knowing this was annoying to you, consider this another annoyance resolved! 🙂
Later,
Jacques.
Be sure to follow Jacques on Twitter @JacqBens

